Role-Based Access Control (RBAC) is a widely-used access control model that governs user access to resources in a system based on their assigned roles. RBAC simplifies access management by granting permissions to users according to their roles and responsibilities, reducing the complexity of individually assigning permissions for each user. Users, roles, and permissions make up RBAC, as well as the hierarchy of roles between them.

Benefits of RBAC
- Simplified Administration: RBAC simplifies access management by grouping users with similar responsibilities into roles, reducing administrative overhead and the risk of human error.
- Enhanced Security: RBAC helps prevent unauthorized access and reduces the attack surface, as users are granted only the necessary permissions for their roles.
- Improved Compliance: RBAC aids in meeting regulatory compliance requirements by ensuring access control policies are well-defined and enforced.
- Flexibility and Scalability: RBAC can accommodate organizational changes easily, such as new job roles or department restructuring, without the need to redefine access permissions for individual users.
- Audit Trail and Accountability: RBAC provides a clear audit trail of actions performed by users based on their assigned roles, facilitating accountability and incident investigation.
Implementing RBAC
- Define Roles and Permissions: Identify the roles needed in the system and assign appropriate permissions to each role.
- Assign Users to Roles: Map users to their respective roles based on their job responsibilities and access requirements.
- Role Hierarchy (Optional): If applicable, establish a role hierarchy to simplify role assignment and inheritance.
- Enforce Least Privilege: Ensure that each role has the minimum necessary permissions for its intended tasks.
- Access Revocation and Review: Regularly review access rights and revoke access when necessary, such as when employees change roles or leave the organization.
- Regular Auditing: Conduct periodic audits to validate that access permissions align with organizational policies and RBAC rules.
Best Practices for ımplementing RBAC
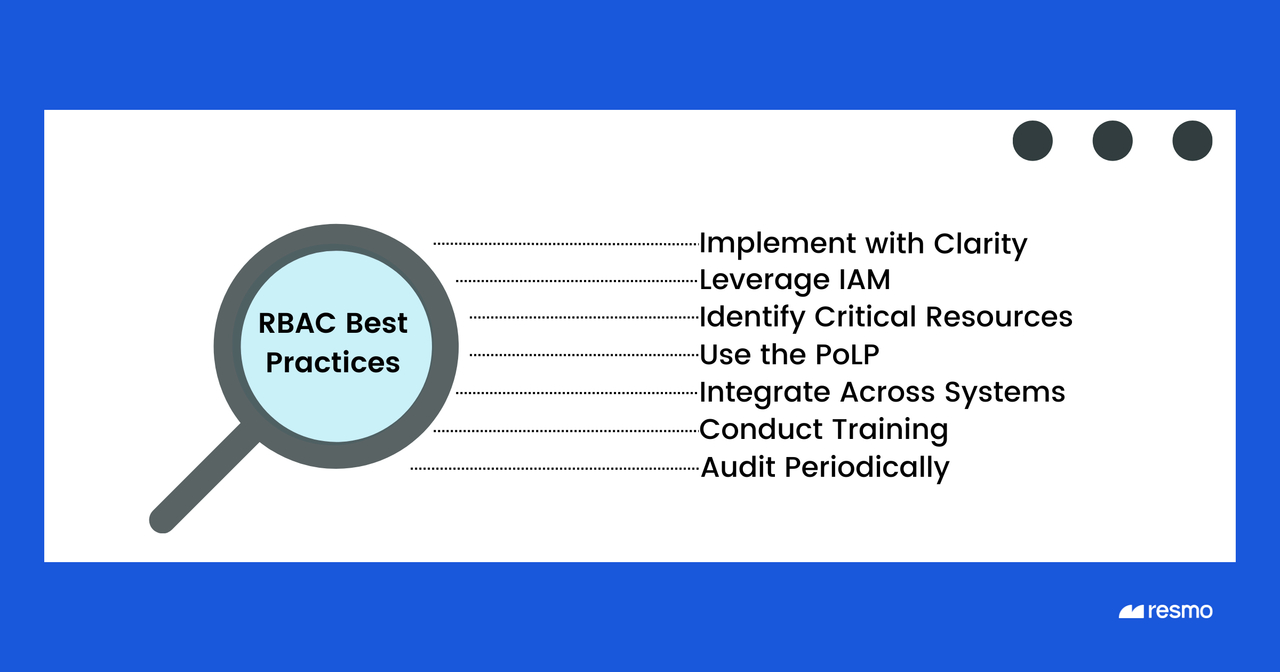
- Implement RBAC with Clarity: Avoid causing unnecessary confusion and workplace irritations when implementing RBAC by ensuring clear communication and understanding among all stakeholders.
- Leverage Identity and Access Management (IAM) System: While not a prerequisite, having an IAM system in place can facilitate RBAC implementation and improve access management.
- Identify Critical Resources: Create a list of resources that require controlled access to determine the roles needed.
- Use the Principle of Least Privilege (POLP): Follow POLP to grant users access only to the actions, software, or files necessary for their job roles.
- Integrate RBAC Across Systems: Ensure RBAC is integrated consistently across all systems throughout the organization to maintain uniform access controls.
- Conduct Training: Provide training to employees to ensure they understand the principles of RBAC and their respective roles and responsibilities.
- Periodic Auditing: Conduct regular audits of roles and access rights to identify and rectify any potential issues, ensuring compliance and security.
RBAC vs. ABAC
RBAC and Attribute-Based Access Control (ABAC) are both access control methods with different approaches. While RBAC grants access based on user roles, ABAC controls access based on a combination of user attributes, resource attributes, action attributes, and environmental attributes. ABAC offers more granular access control and is suitable for complex environments that require precise access management.
Related Terms
- The Principle of Least Privilege (PoLP)
- Identity Security Posture Management
- Privileged Access Management
Suggested Articles







