
40+ Cloud Security Statistics You Need to Know in 2024
With businesses moving to the cloud in droves and fewer companies making their own data centers, security is more critical than ever. The unfortunate truth is that cyber-attacks are also on the rise.
The first thing you should know is that the cloud is not inherently insecure. It can be just as secure or insecure as any other IT environment; it all depends on how carefully you manage your data and applications.
Cloud security is like a game of chess - always think ahead, anticipate the moves of your opponent, and never underestimate the power of a well-executed defense.
This blog covers the current state of cloud security and gives you insight into what you need to be aware of and ready for in the present moment.
Cloud security statistics: Editor’s picks
Gartner, Inc. predicts that global spending on public cloud services by end-users will increase by 20.7% to reach $591.8 billion in 2023, compared to $490.3 billion in 2022. This projected growth rate is greater than the 18.8% forecasted for 2022.
- 69% of organizations admitted to experiencing data breaches or exposures due to multi-cloud security configurations.
- 82% of organizations find managing cloud costs the biggest cloud security challenge, while 79% consider security as their primary challenge.
- Per IBM, the average total cost of a data breach is $4.35M.
- 82% of data breaches included human-related elements, which encompassed social attacks, mistakes, and abuse, according to the report.
- 89% of businesses most affected by cloud security incidents were startups.
The latest cloud security stats to watch out for
Cloud security is constantly evolving, with new technologies and strategies emerging to combat evolving cyber threats. Staying up-to-date on cloud security statistics, facts, and trends can help users stay ahead of the curve and adopt the best practices to secure their cloud infrastructure. Let’s start off by taking a look at the multi-cloud trend.
Multi-cloud security challenges
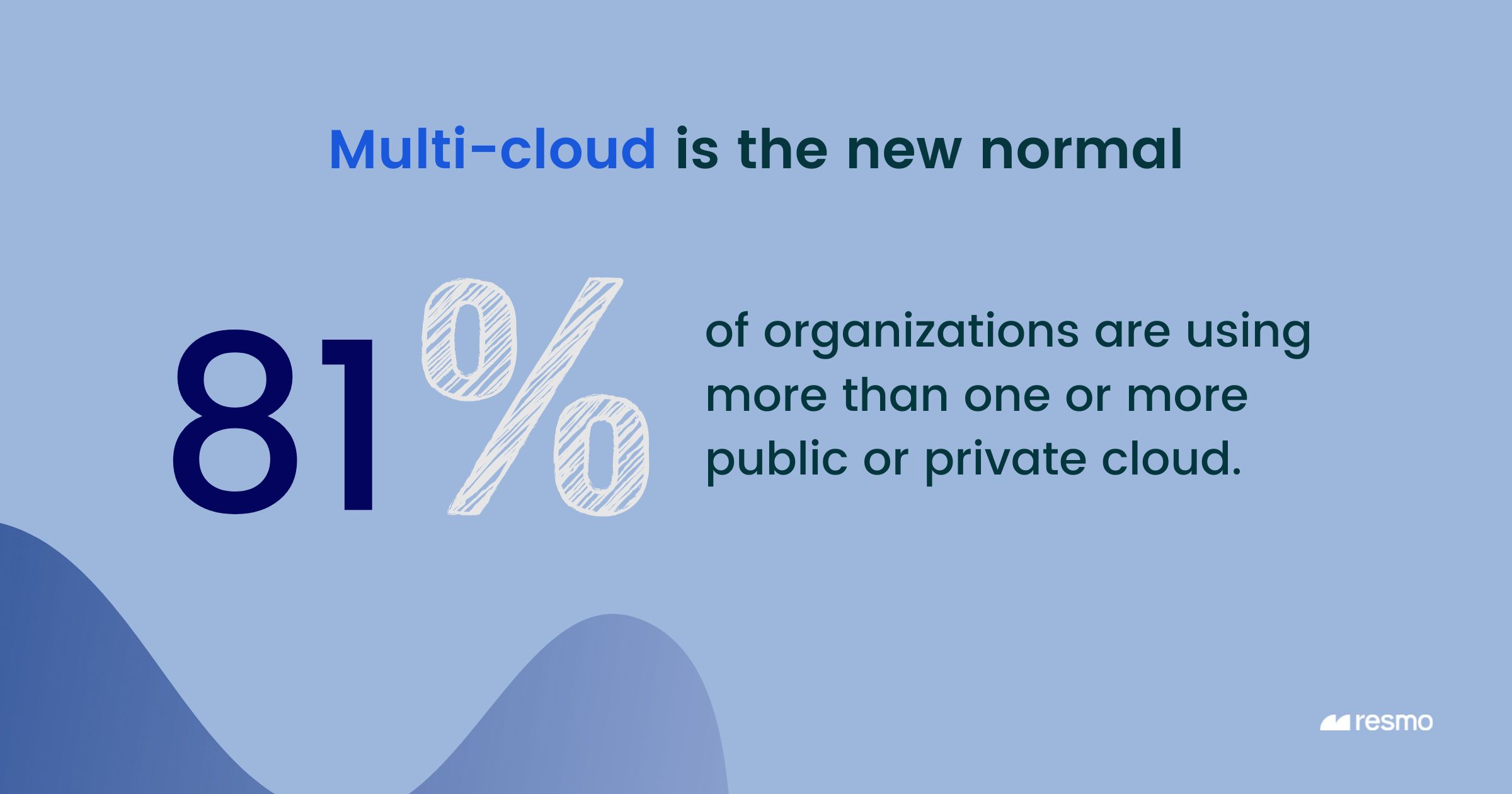
Multi-cloud usage: 81% of organizations are already using multi-cloud.
Maintaining security in the multi-cloud: A report by Radware revealed that despite using multiple security tools to safeguard their cloud applications, 70% of organizations lack confidence in their ability to maintain consistent security measures across on-premise and multi-cloud environments.
Data breach in the multi-cloud: 69% of the surveyed organizations admitted to experiencing data breaches or exposures due to multi-cloud security configurations.
Biggest security obstacle with the multi-cloud: The primary obstacle to securing multi-cloud environments in 2022 was identified as a lack of expertise in deploying and managing a comprehensive solution across all cloud environments.
Additionally, a considerable 37% of respondents across the globe reported that their organizations faced difficulties keeping up with the pace of change when it came to securing their multi-cloud environments. (Source: Statista)
Cloud security challenges
The top cloud security challenges organizations face have changed in the last decade, with managing cloud spend (82%) overtaking security (79%) to claim the number one spot. This change in priorities could be attributed to the fact that organizations have gained more confidence in cloud security measures, resulting in greater adoption of cloud services and, subsequently, more cloud spend. (Flexera)

The report expands to nine different prominent cloud security challenges faced by all organizations that participated in the survey:
- Managing cloud spend (82%)
- Security (79%)
- Lack of resources/expertise (78%)
- Governance (71%)
- Compliance (73%)
- Managing software licenses (72%)
- Cloud migration (66%)
- Central cloud team/business unit responsibility balancing (67%)
- Managing multi-cloud (66%)
A comprehensive cloud strategy that addresses these challenges can help organizations unlock the full potential of the cloud while ensuring security and cost-effectiveness.
State of data breach in the cloud

Roughly half of all data breaches take place in the cloud.
Although 45% of data breaches took place in the cloud, organizations that use a hybrid cloud approach experienced lower average costs of data breaches, at USD 3.80 million, compared to organizations that exclusively used public or private cloud models.
According to IBM, the average data breach cost in organizations using a private cloud is $4.24M.
The average data breach cost for organizations using a public cloud (i.e., AWS, GCP, Azure) is $5.02M.
The frequency of cloud attacks
Per Snyk’s report, 80% of organizations encountered a significant security incident related to their cloud infrastructure within the past year.
Major cloud incidents experienced were:
- Cloud data breach (33%)
- Cloud data leak (28%)
- Environment intrusion (27%)
- Cryptomining (23%)
- Serious compliance violation (25%)
- Failed audit (15%)
- System downtime due to misconfiguration (34%)
Suggested reading: Common Amazon S3 Bucket Misconfigurations.
Cloud customers encountered several significant security incidents over the past year, including data breaches, data leaks, and unauthorized access to their cloud environments, among others.
It is alarming to note that 25% of survey respondents expressed concern about experiencing a cloud data breach that went undetected.
Such cloud security incidents can lead to dire consequences, such as:
- Penalties for failing audits and compliance violations
- Unauthorized cryptomining that can rack up substantial cloud bills
- Loss of business due to system downtime.
As such, organizations must implement comprehensive cloud security measures to safeguard their cloud environments and minimize the impact of any potential security incidents.
Cloud misconfiguration statistics
Organizations with high-maturity cloud security consider the identification of misconfigurations in the cloud as their top priority.
In fact, cloud resource misconfigurations are a major concern for any organization that uses cloud services. These mistakes typically happen when organizations set up and deploy their cloud infrastructure using cloud provider consoles or infrastructure as code.
- Check Point's 2022 Cloud Security Report revealed that 27% of businesses had encountered a security breach in their public cloud infrastructure over the past year. Among these incidents, almost a quarter (23%) were due to cloud infrastructure's security misconfigurations.
The primary risk arises from a combination of errors made during deployment and unauthorized changes made after deployment, which can lead to various cloud security incidents. It's crucial to be proactive in monitoring and managing cloud configurations to prevent security risks and protect sensitive data.

Cloud security incidents stretch across various parts of the cloud. The study conducted by Synk shows some of the main areas as the following:
- IAM misconfiguration (17%)
- Object storage misconfiguration (20%)
- Insecure use of data backups (23%)
- Insecure API keys (20%)
- Lack of monitoring (20%)
Also, read API Security Best Practices to ensure your API key security.
Identity and Access
When it comes to misconfiguration, setting up access permissions is also a concern. According to a report, 83% of organizations have experienced at least one cloud data breach related to access, and about half of those breaches (50%) have been attributed to access permissions.
One of the main reasons for this is that over half of the organizations (52%) don't have visibility into which resources a user can access or the level of permission granted.
As a result, it's crucial to have a clear understanding of access permissions and closely monitor user access to prevent security breaches.
You might also like IAM Best Practices for Security.
Human factor in cloud security attacks
- A staggering 82% of breaches involved human-related factors, such as social attacks, errors, and misuse.
Recent cybersecurity statistics highlight the critical role of the human element in security breaches. This is a concerning trend that emphasizes the need for increased employee awareness training and strict security protocols.
- Another alarming statistic is the 13% increase in ransomware breaches, more than the combined total of the last five years.
This trend underscores the increasing threat of ransomware attacks and the importance of implementing robust security measures.
- Moreover, 62% of incidents in the system intrusion pattern involved threat actors compromising partners.
This finding highlights the importance of secure third-party relationships and reinforces the need for organizations to regularly assess and mitigate partner-related risks.
Phishing
Approximately 51% of organizations have indicated that phishing is the most prevalent approach attackers use to obtain legitimate cloud credentials. Similarly, it has been reported that phishing is involved in approximately 25% of all data breaches, where scammers pose as trustworthy sources, such as banks, mobile phone companies, postal delivery services, or friends.
Who are the most affected by cloud security incidents?
Major cloud security incidents impacted customers, regardless of size or industry sector. Among those affected, fast-growing startups were hit the hardest, with 80% experiencing such incidents.
Public sector entities, which included government agencies and non-profit organizations, also suffered nearly the same impact. In contrast, enterprise companies were less affected, most likely because they invested more resources in cloud security and focused more on infrastructure as code security.
The State of Cloud Security Report by Snyk shows:
- 89% of businesses affected by cloud security incidents were startups.
- Public sector (88%)
- Enterprises (74%)
- Small to medium businesses (68%)
Cloud security with Resmo
Resmo simplifies the process of identifying and responding to cloud vulnerabilities, thereby making the job of IT and security teams more manageable through automation. Connect your cloud service and SaaS applications to start monitoring your assets, changes, users, and vulnerabilities in one place. It’s free to get started. Give it a go and see Resmo in action!
Worth the read:







