
Azure AD Best Practices Checklist for Secure Identities
Organizations rely heavily on cloud-based services and applications to conduct their day-to-day operations in today's digital landscape. As businesses continue to embrace the cloud, the need for a robust and secure identity and access management (IAM) solution has never been more critical. Azure Active Directory (Azure AD) is a comprehensive IAM service from Microsoft that provides a powerful, scalable, and secure solution for managing and protecting user identities and access to resources.
However, simply implementing Azure AD is not enough. To ensure the security and efficiency of your organization's IAM strategy, it is essential to follow Azure AD best practices that cover every aspect. In this blog post, we will dive into some of the most critical Azure AD best practices to help you strengthen your IAM strategy, protect sensitive data, and maintain compliance.
We will discuss topics such as role-based access control, multi-factor authentication, conditional access, password management, single sign-on, and more. By following these best practices, you can create a more secure and streamlined environment that empowers your users while safeguarding your organization's valuable assets. So, let's get started!
1. Enable Multi-Factor Authentication (MFA)

The top of Azure AD best practices checklist is reserved for MFA, as in any other cloud-based service. Azure AD Multi-Factor Authentication (MFA) is a powerful security feature that enhances the protection of your organization's resources by requiring users to provide two or more forms of authentication during sign-in. The authentication methods used in Azure AD MFA are based on:
- Something you know - typically a password.
- Something you have - a trusted device that's not easily duplicated, like a phone or hardware key.
- Something you are - biometrics such as a fingerprint or face scan.
By combining these different authentication methods, Azure AD MFA ensures that access to resources is only granted to authorized individuals, reducing the risk of unauthorized access due to compromised passwords.

Azure AD MFA also integrates seamlessly with self-service password reset, allowing users to register for both features in a single step. This streamlines the user experience and further secures the password reset process.
One of the key advantages of Azure AD MFA is that it doesn't require any modifications to your existing apps and services. The verification prompts are integrated into the Azure AD sign-in process, automatically requesting and processing the MFA challenge when needed.
To quickly enable MFA for all users, you can use security defaults in Azure AD tenants. This configuration enables the Microsoft Authenticator app for all users by default. Additionally, you can enable Azure AD MFA to prompt specific users and groups for additional verification during sign-in.
For more advanced and granular controls, you can leverage Conditional Access policies to define specific events or applications that require MFA. These policies can be configured to allow regular sign-in when a user is on the corporate network or a registered device but prompt for additional verification factors when the user is remote or on a personal device.
2. Configure Password Management
Recent updates from Microsoft have led to revised password policy guidance, which no longer mandates password expiration. However, small and medium-sized enterprises (SMEs) with regulatory requirements or those lacking Multi-Factor Authentication (MFA) and Conditional Access (CA) configurations need to remain cautious and continue updating passwords as needed. Changing passwords might also be necessary in cases where you suspect an identity has been hijacked.
With the increasing prevalence of malware-less attacks targeting cloud IDs and the fact that 75% of cloud breaches are due to compromised identities, adopting a Zero Trust posture is no longer optional. Consider deploying Extended Detection and Response (XDR) solutions from a trusted vendor or opting for Microsoft Identity Protection if you prefer the Microsoft stack.
To maintain a secure environment, consider implementing the following best practices:
- Set up self-service password reset (SSPR) with two authentication methods. Avoid using security questions, as attackers can often gather relevant information from open sources on the web or third-party breaches. Note that Microsoft charges extra for on-premises write-back.
- Maintain consistent password policies across all environments, both on-premises and cloud-based. Microsoft provides extensive documentation for implementing an agent-based approach to enforce Azure AD password protection on Active Directory Domain Services (AD DS) without exposing your domain controller to the web or forcing network changes. However, this requires proficiency in modifying AD settings.
By embracing a Zero Trust posture and following these best practices, you can reduce the risk of compromised identities and maintain a more secure environment for your organization. Remember that a robust security strategy involves not just configuring MFA and CA, but also implementing a comprehensive approach to password management and protection.
Suggested reading: Latest Cloud Computing Trends
3. Enable Single Sign-On
Single Sign-On (SSO) is a valuable feature that can boost security through modern authentication protocols, improve user experience, and reduce management overhead. SSO enables users to access multiple applications and services using a single set of credentials, streamlining the authentication process.
Azure AD provides pre-built integrations via the Azure AD application gallery, as well as support for SAML and OAuth 2.0 SSO protocols for manual configuration. Although Microsoft does not support the AAA protocol RADIUS, which many network appliances rely on for access control, alternative solutions like cloud RADIUS or the Microsoft NPS server role can be used to overcome this limitation.

In hybrid deployments, all Azure AD tiers can access native Windows apps using authentication protocols such as Kerberos, NTLM, LDAP, RDP, and SSH. However, advanced identity protection features like Conditional Access are limited to Azure AD Premium P1 and P2 offerings, which include Azure AD Application Proxy and secure hybrid partnership integrations. These additional services help extend modern security features to legacy applications.
It's worth noting that Microsoft previously imposed restrictions on the number of SSO applications per user for its free tier; however, this policy may be subject to change. By enabling SSO in your Azure AD environment, you can not only simplify the user experience but also enhance security and reduce administrative overhead.
4. Streamline Access Lifecycle Management

Effectively managing access lifecycle is crucial for maintaining a secure and compliant environment, especially when integrating on-premises Active Directory (AD) with Azure AD. By streamlining the processes of provisioning, managing, and deprovisioning access to resources, you can ensure that the right users have access to the right resources at the right time while minimizing the risk of unauthorized access. Here's how to optimize access lifecycle management in a hybrid environment:
- Leverage Azure AD Connect: Synchronize users from your on-premises AD to Azure AD using Azure AD Connect. This ensures consistency in user identities and group memberships, providing centralized management. Microsoft also supports non-Microsoft identities for access control, although extra costs might apply.
- Plan migrations carefully: If your organization previously deployed Active Directory Federation Services (AD FS) before Azure AD was available, take a cautious and well-planned approach when migrating users from AD FS to Azure AD. Avoid impulsive decision-making that could lead to disruptions to system availability or unforeseen issues.
- Provision access: Grant appropriate access to necessary resources promptly when onboarding new users or assigning them to new projects. Use Azure AD's automated provisioning capabilities to create and configure user accounts based on predefined templates and rules.
- Manage access: Continuously monitor and manage user access to resources to ensure that it remains aligned with their roles and responsibilities. Implement Role-Based Access Control (RBAC) to assign granular permissions based on job functions and review access rights regularly.
- Deprovision access: Revoke access to resources promptly when users change roles, leave the organization, or when a project concludes. Establish a formal offboarding process that includes revoking access to applications, services, and data.
- Harden Active Directory: For organizations choosing a hybrid identity management approach, it's crucial to harden and maintain the on-premises Active Directory for optimal security. Follow best practices for managing and maintaining AD, such as limiting administrative privileges and avoiding running day-to-day tasks as a domain administrator.
5. Leverage Role-Based Access Control

Azure AD provides both built-in and custom user roles, enabling you to implement Role-Based Access Control (RBAC) across all subscription tiers. This approach helps establish a Zero Trust security posture and adheres to the principle of least privilege. However, keep in mind that RBAC requires consistent manual input and maintenance.
To effectively utilize RBAC and enhance your organization's security, consider the following Azure AD RBAC best practices:
- Minimize privileged accounts: Reduce the number of accounts with elevated access rights to minimize potential security risks.
- Manage and monitor access: Establish a plan for controlling and monitoring user access to resources, ensuring that permissions remain aligned with users' job functions.
- Limit global administrator accounts: Use alternative roles such as billing administrator, global reader, helpdesk administrator, and license administrator to further limit the number of high-privilege accounts.
- Avoid syncing high-privilege accounts: Refrain from syncing high-privilege accounts from on-premises AD to Azure AD, which helps maintain a separation of duties.
- Review external collaboration settings: Pay close attention to external collaboration settings, considering restrictions on guest access to shared files and third-party storage. This can help streamline official channels and reduce potential security risks.
- Utilize security groups: Leverage security groups for users to enhance application security and lower administrative overhead. Keep in mind that this capability is limited to Azure AD Premium 1 (P1) and Premium 2 (P2) accounts. Aim to avoid assigning resources directly to users and employ identity protection when possible.
6. Manage Connected Applications

Managing connected applications in your Azure AD environment involves careful consideration of various factors, including provisioning, access control, and single sign-on (SSO). Here are some additional best practices to help you manage connected applications effectively:
- Use group assignment for applications: By default, application provisioning is on a per-user basis. However, if you have a P1, P2, or equivalent Azure AD subscription, you can leverage group assignment to simplify management and ensure that applications do not inadvertently grant excessive access through RBAC.
- Automate application provisioning: Utilize automation tools and processes for application provisioning, including initial user population and incremental updates. This can help streamline provisioning tasks and ensure consistency across your environment.
- Optimize attribute mapping: Azure AD offers several options for attribute mapping from various identity sources via SCIM endpoints, cloud resources, or the Azure AD Provisioning agent. Ensure that your chosen method aligns with your organization's requirements and infrastructure.
- Centralize identity management: Siloed identities can complicate identity management and increase security risks. Implement SSO to centralize identity management, either through Azure AD or a system or service that integrates with it. This will help reduce technical overhead and improve security.
You might also like Kubernetes Security Best Practices.
7. Implement Conditional Access
Conditional Access is a powerful feature of Azure AD that combines various signals to make decisions and enforce organizational policies. It serves as the core of the identity-driven control plane, enabling administrators to strike a balance between user productivity and organizational asset protection.
Conditional Access policies function as if-then statements, specifying the actions users must complete to access certain resources. For example, a payroll manager may be required to perform multi-factor authentication before accessing the payroll application. These policies come into effect after first-factor authentication, providing an additional layer of security without being the first line of defense against attacks like denial-of-service (DoS).
By implementing Conditional Access policies, administrators can tailor access controls based on specific conditions, empowering users to work efficiently without compromising security. This adaptive approach ensures that the right access controls are applied when necessary, helping organizations maintain a secure environment.
Keep in mind that Conditional Access policies should be used in conjunction with other security measures, such as multi-factor authentication and identity protection, to create a comprehensive security strategy. Regularly review and update policies as your organization's needs evolve, and leverage Azure AD's reporting and auditing features to monitor policy enforcement and maintain compliance.
8. Consider the Worst-Case Scenario
Preparing for the worst-case scenario is a crucial aspect of maintaining a secure and resilient Azure AD environment. By anticipating potential security threats and planning for the unexpected, you can minimize the impact of breaches or other incidents, ensuring that your organization can recover quickly and effectively.
Here are some steps to help you prepare for the worst-case scenario in your Azure AD environment:
- Develop a comprehensive disaster recovery plan: Create a detailed disaster recovery plan that outlines the steps your organization will take in the event of a security breach, natural disaster, or other disruptive events. This plan should cover data backup and restoration, emergency communication protocols, and the roles and responsibilities of team members during the recovery process.
- Implement strong backup and recovery procedures: Regularly back up your Azure AD data and ensure that recovery procedures are in place and tested. This may include backing up critical data to offsite locations, utilizing Azure AD's built-in recovery features, and employing third-party solutions for added redundancy.
- Train your team: Educate your IT staff and other team members about the disaster recovery plan and their responsibilities during an incident. Conduct regular training sessions and drills to ensure everyone is familiar with the process.
- Establish an emergency access Global Admin account: Create a "break-the-glass" Global Admin account that can be used during network outages and system downtime. This account should be excluded from Conditional Access and Multi-Factor Authentication. Ensure the credentials are stored securely and use a highly complex password.
By following these steps, you can establish a strong foundation with the appropriate entitlements, attributes, and processes to prepare your Azure AD for application provisioning and ensure your organization is prepared for the worst-case scenario.
9. Avoid Phishing
Azure AD's default settings allow all users to access the admin portal and register custom Single Sign-On (SSO) applets. Attackers are aware of this and may exploit OAuth in phishing attacks, potentially bypassing Multi-Factor Authentication (MFA). To mitigate this risk, it's essential to adhere to the principle of least privilege, ensuring that only users who require access are granted it.
Consider the following best practices to minimize security risks:
- Restrict user-driven application consent: Limit the ability of users to register and manage custom SSO applets. By doing so, you can reduce the attack surface and maintain tighter control over application permissions.
- Set permissions classifications: Apply "low impact" permissions classifications to users and group owners to restrict unnecessary access to sensitive data and resources.
- Assess compliance boundaries: Be cautious when dealing with compliance requirements outside of the Microsoft ecosystem, and work closely with compliance experts to ensure adherence to relevant standards.
- Seek expert guidance: Azure AD can be complex, and it's not uncommon for organizations to require assistance from experienced consultants. Allocate the budget for consulting services to ensure the successful implementation and management of your Azure AD environment.
- Monitor suspicious OAuth authorization requests: Invest in additional security solutions, such as Microsoft Cloud App Security or third-party alternatives like CrowdStrike Falcon Identity Protection, to receive alerts about suspicious OAuth requests and proactively address potential threats.
10. Secure Hybrid Environments
Many organizations opt for a hybrid approach, where they maintain a combination of on-premises Active Directory (AD) and Azure Active Directory (AAD) environments. This approach provides flexibility and enables the smooth transition of resources to the cloud. However, it also introduces additional security challenges, as organizations must ensure that both their on-premises and cloud-based infrastructures are properly secured.
Here are some best practices for securing hybrid environments:
- Synchronize identities: Use Azure AD Connect to sync your on-premises AD with Azure AD, ensuring consistent identity management across both environments. Regularly monitor and maintain the sync process to prevent inconsistencies that could lead to security vulnerabilities.
- Implement Single Sign-On (SSO): Enable SSO to streamline access to both on-premises and cloud resources, reducing the risk of credential theft and simplifying identity management.
- Harden your on-premises Active Directory: Strengthen your on-premises AD security by applying security patches, monitoring for vulnerabilities, and implementing best practices for access management, such as the principle of least privilege.
- Extend Conditional Access policies: Apply Conditional Access policies consistently across both on-premises and cloud environments, ensuring that users are required to meet the same security standards regardless of where the resources are hosted.
- Monitor and respond to threats: Implement robust monitoring and threat detection tools for both on-premises and cloud environments and establish a response plan to quickly address security incidents.
- Encrypt data: Use encryption both in transit and at rest to protect sensitive data, whether it's stored on-premises or in the cloud.
- Utilize Azure AD Application Proxy: Leverage Azure AD Application Proxy or secure hybrid partnership integrations to extend modern security features to legacy applications.
11. Utilize Azure Azure AD Privileged Identity Management (PIM)

Azure AD Privileged Identity Management (PIM) is an essential tool for enhancing security by managing, monitoring, and auditing access to critical resources. Here are some key best practices for effectively utilizing PIM:
- Use Just-in-Time (JIT) access to grant temporary, time-bound access instead of permanent privileged access.
- Enforce the principle of least privilege by assigning appropriate roles and permissions.
- Require Multi-Factor Authentication (MFA) for privileged role activations.
- Implement approval workflows for privileged access requests.
- Monitor and audit privileged access using PIM's reporting features.
- Set up alerts for suspicious activities and high-risk events.
- Provide training and guidance to your team on PIM usage and security best practices.
12. Audit Your Azure AD Security Regularly
Regularly auditing your Azure AD security is crucial to maintain a strong security posture and ensuring that your organization's access controls are up to date. This practice helps you identify potential vulnerabilities, monitor compliance, and take appropriate actions to mitigate risks. Here are some steps to follow when auditing your Azure AD security:
- Review role assignments: Periodically assess role assignments to ensure that users have the appropriate permissions for their job responsibilities. Remove unnecessary access and update roles to align with users' current responsibilities.
- Monitor access patterns: Analyze access logs to detect unusual or suspicious behavior that may indicate security risks or potential breaches. Investigate any anomalies and take corrective actions as needed.
- Validate compliance with policies: Ensure that your organization adheres to internal security policies and external regulatory requirements. Regularly review and update these policies to maintain compliance.
- Assess Multi-Factor Authentication (MFA) usage: Verify that MFA is enabled and properly configured for all privileged accounts and sensitive resources. Address any gaps or inconsistencies to strengthen your security.
- Evaluate Conditional Access policies: Review your Conditional Access policies to ensure they are effectively controlling access based on user, device, location, and risk factors. Update policies as necessary to address evolving security requirements.
- Inspect connected applications: Regularly assess the security of connected applications and ensure that they follow best practices for access control and data protection. Revoke access to any applications that no longer meet your security standards.
- Test your incident response plan: Conduct regular tests and simulations to evaluate the effectiveness of your incident response plan. Update the plan as needed to address any identified gaps or weaknesses.
How Resmo Helps Keep Up with Azure AD Best Practices
Resmo is a powerful tool that enables companies using Azure AD, along with other cloud services and cloud-based apps, to efficiently manage and monitor their Azure AD assets, ensuring compliance with best practices. By providing a unified platform for visualizing, querying, and tracking changes, Resmo simplifies the process of maintaining a secure and well-organized Azure AD environment.

Here's how Resmo helps companies keep up with Azure AD best practices:
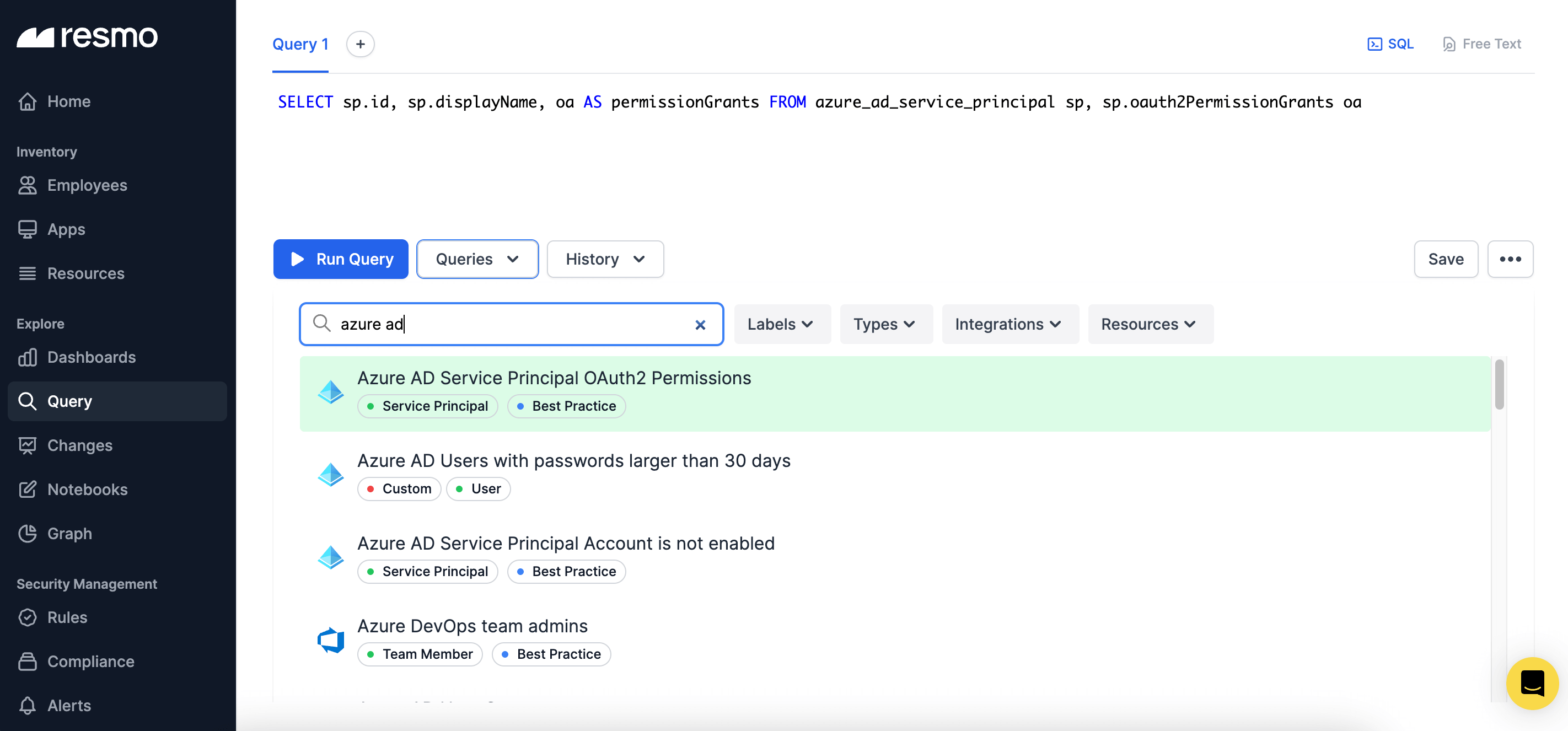
- Centralized asset visualization: Resmo allows you to see all your Azure AD assets, such as users, organizations, authorization policies, and OAuth2 Permission Grants, in one place. The graph view provides an intuitive visualization of assets in context, making it easy to identify relationships and dependencies.
- Querying capabilities: Resmo's querying feature enables you to quickly search and filter your Azure AD assets based on specific criteria. This powerful tool simplifies the process of auditing and reviewing your access controls and permissions.
- Change tracking and actor identification: With Resmo, you can monitor changes to your Azure AD assets and identify the actors responsible for those changes. This feature is invaluable for maintaining accountability and ensuring that your security policies are being followed.
- Alerts for asset changes: Resmo allows you to set up alerts for changes in your Azure AD assets, ensuring that you're notified of any potential security risks or policy violations. This proactive approach to monitoring helps you quickly address issues and maintain a secure environment.
- Enhanced compliance: By providing a unified platform for managing and monitoring your Azure AD assets, Resmo makes it easier to maintain compliance with internal security policies and external regulatory requirements.
Frequently Asked Questions
What are the 4 types of Azure AD?
Azure Active Directory (Azure AD) is Microsoft's cloud-based identity and access management service. It offers four different editions to cater to the varying needs of organizations. These four types of Azure AD are:
- Azure AD Free
- Azure AD Office 365 Apps
- Azure AD Premium P1
- Azure AD Premium P2
What are the Azure Active Directory recommendations?
Azure Active Directory (Azure AD) is a crucial component in managing identities and access within an organization's cloud environment. To maximize security and efficiency, consider the following Azure AD recommendations:
- Enable Multi-Factor Authentication (MFA)
- Implement Conditional Access
- Configure Password Management
- Utilize Role-Based Access Control (RBAC)
- Enable Single Sign-On (SSO)
- Manage Connected Applications
- Secure Hybrid Environments
- Implement Azure AD Privileged Identity Management (PIM)
- Protect Against Phishing
- Audit Your Azure AD Security Regularly
What are the 3 main identity types used in Azure AD?
In Azure Active Directory (Azure AD), there are three main identity types used to manage and organize users and resources: Cloud identities, Synchronized identities, and Federated identities.
What are the most sensitive Azure AD roles?
Sensitive Azure AD roles are those that grant elevated permissions and administrative capabilities. Organizations must closely manage and monitor access to these roles to ensure security and maintain the principle of least privilege. Some of the most sensitive Azure AD roles include:
- Global Administrator
- Privileged Role Administrator
- SharePoint Administrator
- Exchange Administrator
- Security Administrator
- Application Administrator
Interested in improving your cloud security knowledge? Take a look at more articles from Resmo.
Read on:







